Wael Ghonim, cited in Rebecca MacKinnon, Consent of the Networked: The Worldwide Struggle for Internet Freedom (New York City: Basic Books, 2012), xx.
Brandon Teddler, “To The Cloud!,” Ezine Mark, February 20, 2012.
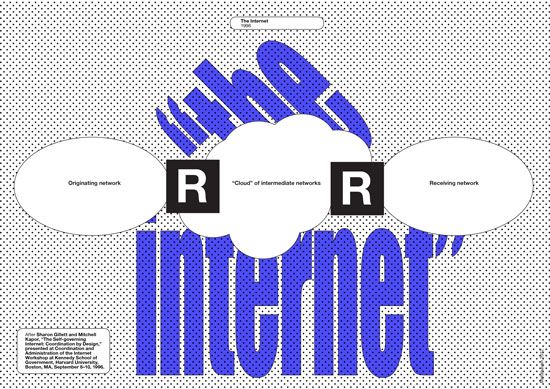
Sharon Gillett and Mitchell Kapor, “The Self-governing Internet: Coordination by Design,” presented at Coordination and Administration of the Internet Workshop at Kennedy School of Government, Harvard University, Boston, MA, September 8–10, 1996. See →.
John Markoff, “An Internet Critic Who Is Not Shy About Ruffling the Big Names in High,” New York Times, April 9, 2001. See →.
Eric Schmidt, “Conversation with Eric Schmidt Hosted by Danny Sullivan,” Search Engine Strategies Conference, August 9, 2006. See →.
“Amazon: The Walmart of the Web,” The Economist, October 1, 2011. See →.
Nathan Eddy, “Cloud Computing to Drive Storage Growth: IDC Report,” eWeek, October 21, 2011.
Nick Bilton, “Data storage server, and founder, move quickly.” International Herald Tribune, August 28, 2012.
Zack Whittaker, “Summary: ZDNet’s USA PATRIOT Act Series,” ZDNet, April 27, 2011. See →.
Jeffrey Rosen, “Too Much Power,” New York Times, September 8, 2011. See →.
Matthew C. Waxman, “Extending Patriot Act Powers,” interview by Jonathan Masters, www.cfr.org, February 22, 2012. See →.
Saskia Sassen, Territory, Authority, Rights. From Medieval to Global Assemblages, Princeton and Oxford: Princeton University Press, 2006 (2008), 180.
Paul Taylor, “Privacy Concerns Slow Cloud Adoption,” Financial Times, August 2, 2011. See →.
Lucian Constantin, “Google Admits Handing over European User Data to US Intelligence Agencies,” Softpedia, August 8, 2011. See →.
Winston Maxwell, and Christopher Wolf, “A Global Reality: Governmental Access to Data in the Cloud,” A Hogan Lovells White Paper, May 23, 2012. See →.
Mike Masnick, “Senators Reveal That Feds Have Secretly Reinterpreted The PATRIOT Act,” Techdirt, May 26, 2011. See →.
Kim Zetter, “Unknown Tech Company Defies FBI In Mystery Surveillance Case,” Wired, March 14, 2012. See →.
Ryan Singel, “Egypt Shut Down Its Net With a Series of Phone Calls.” Wired, January 28, 2011. See →.
Claire Connelly and Lee Taylor, “FBI Shuts down Megaupload.com, Anonymous Shut down FBI,” News.com.au, January 20, 2012. See →.
Ibid.
See Jennifer Granick, “Megaupload: A Lot Less Guilty Than You Think,” Center for Internet and Society at Stanford Law School, January 26, 2012. See →.
David Kravats, “Uncle Sam: If It Ends in .Com, It’s .Seizable,” Wired, March 6, 2012. See →.
Michael Geist, “All Your Internets Belong to US, Continued: The Bodog.com Case,” michaelgeist.ca, March 6, 2012. See →.
Ronald Deibert, John Palfrey, Rafal Rohozinski, Jonathan Zittrain (eds.), Access Controlled: The Shaping of Power, Rights, and Rule in Cyberspace (Cambridge, Massachusetts: The MIT Press, 2010), 6.
Ibid., 11.
Ellen Nakashima, “A Story of Surveillance,” The Washington Post, November 7, 2007. See →.
Ibid.
Dan Levine, “US Court Upholds Telecom Immunity for Surveillance,” Thomson Reuters, December 29, 2011. See →.
Ronald Deibert et. al., Access Controlled, 381.
Declan McCullagh, “FBI: We Need Wiretap-Ready Web Sites – Now,” CNET, May 4, 2012. See →.
Geoff White, “‘Black Boxes’ to Monitor All Internet and Phone Data,” Channel 4, June 29, 2012. See →.
Alex Wawro, “What Is Deep Packet Inspection?,” PC World, February 1, 2012. See →.
Declan McCullagh, “Report: Feds to Push for Net Encryption Backdoors,” CNET, September 27, 2010. See →.
See →.
Alexis Madrigal, “Why Facebook and Google’s Concept of ‘Real Names’ Is Revolutionary,” The Atlantic, August 5, 2011. See →.
“Amazon.com Help: Pen Names and Real Names,” amazon.com. See →.
Declan McCullagh, “Obama to Hand Commerce Dept. Authority over Cybersecurity ID,” CNET, January 7, 2011. See →.
Elizabeth Kolbert, “The Things People Say,” The New Yorker, November 2, 2009. See →.
Cass R. Sunstein, Republic.com 2.0, (Princeton and Oxford, Princeton University Press, 2007), 44.
Cass R. Sunstein, Adrian Vermeule, “Conspiracy Theories.” Harvard University Law School Public Law & Legal Theory Research Paper Series, Paper No. 199, University of Chicago Law School, 2008, 22. See →.
Michael Kan, “Beijing to Require Users on Twitter-like Services to Register With Real Names,” PC World, December 16, 2011. See →.
Shiv Malik, “Facebook Accused of Removing Activists’ Pages,” The Guardian, April 29, 2012. See →.
Tim Bradshaw, “Mark Zuckerberg Friends David Cameron,” Financial Times, June 21, 2012. See →.
MacKinnon, Consent of the Networked, xxii.
“Internet Freedom.” The prepared text of U.S. of Secretary of State Hillary Rodham Clinton's speech, delivered at the Newseum in Washington, D.C. Foreign Policy, January 21, 2010. See →.
Evgeny Morozov, “Is Hillary Clinton launching a cyber Cold War?” Foreign Policy Net.Effect, January 21, 2010. See →.
See →.
See →.
Tim Wu, “Network Neutrality, Broadband Discrimination.” Journal of Telecommunications and High Technology Law, Vol. 2, p. 141, 2003. See →.
Joichi Ito, “Weblogs and Emergent Democracy.” See →.
On a related note, cyberlaw professor Jonathan Zittrain in 2008 wrote The Future Of The Internet—And How To Stop It, a book focusing on the rise of the web's “tethered appliances,” which, like North Korean radio sets, can be attuned to exclude or disregard certain content, and are designed not to be tinkered with by their users. Zittrain argued that such closed service appliances—emphatically including design icons like iPods and iPhones, for example—would in fact contribute to stifle the generative and innovative capacity of the web. See Jonathan Zittrain, The Future Of The Internet—And How To Stop It, New Haven and London: Yale University Press, 2008.
Christina Bonnington and Spencer Ackerman, “Apple Rejects App That Tracks U.S. Drone Strikes.” Wired, August 30, 2012. See →.
Nick Wingfield, “Apple Rejects App Tracking Drone Strikes.” New York Times Blog, August 30, 2012. See →.
MacKinnon, ibid., 119.
Gregg Keizer, “Apple boots WikiLeaks app from iPhone store.” Computerworld, December 21, 2010. See →.
Written by Daniel van der Velden and Vinca Kruk. Research assistant: Alysse Kushinski. Design assistant: Rasmus Svensson. All images courtesy of Metahaven. Metahaven 2012.
→ Continued in “Captives of the Cloud: Part II”